Context
The scheme was first published by Whitfield Diffie and Martin Hellman in 1976, but in 1997 it was revealed that James H. Ellis,[4] Clifford Cocks, and Malcolm J. Williamson of GCHQ, had previously, in 1969,[5] shown how public-key cryptography could be achieved
This key can then be used to encrypt subsequent communications using a symmetric key cipher.
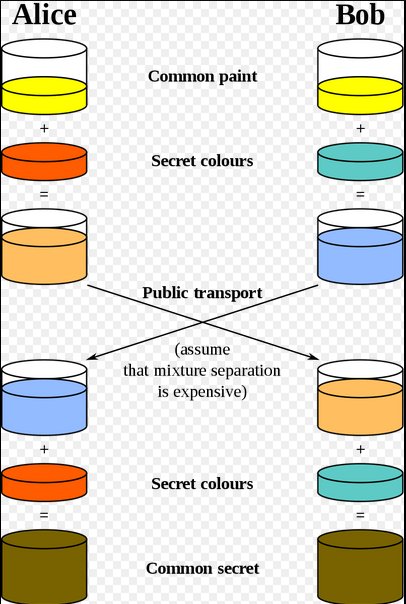
You're not sharing information during the key exchange, you're creating a key together.
ELI5
A Sample Key Exchange Run The chart below depicts who knows what, again with non-secret values in blue, and secret values in red. Here Eve is an eavesdropper – she watches what is sent between Alice and Bob, but she does not alter the contents of their communications.
- g = public (prime) base, known to Alice, Bob, and Eve. g = 5
- p = public (prime) modulus, known to Alice, Bob, and Eve. p = 23
- a = Alice's private key, known only to Alice. a = 6
- b = Bob's private key known only to Bob. b = 15
- A = Alice's public key, known to Alice, Bob, and Eve. A = ga mod p = 8
- B = Bob's public key, known to Alice, Bob, and Eve. B = gb mod p = 19
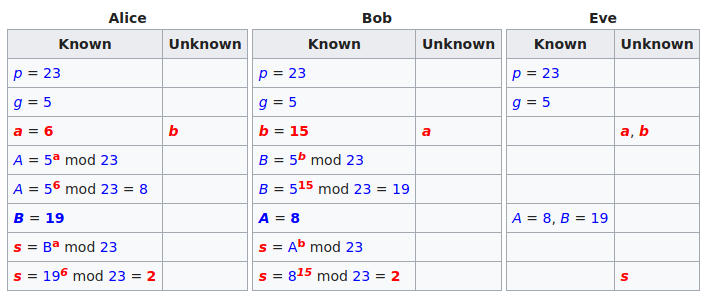
Now s is the shared secret key and it is known to both Alice and Bob, but not to Eve.